The Insanity of “Good” Password Security

There was a little discussion on password limitations over on Google Plus after my post on Two Factor Authentication and Password Limitations. I thought it worth exploring some of the other issues with password security in a little more depth. I will try to keep the discussion as non-technical as possible though.
The short version is if you’re not providing an additional layer of something; be that two factor authentication, biometrics, RSA tokens or whatever; in addition to passwords, you’re simply not taking security seriously. Passwords are past their sell-by date.
First, a question. How many Internet based accounts do you have?
Chances are, it’s far more than you might first think, and will be a lot. 20? 50? More?
Are you including all the websites you once signed up for but forgot about, or can’t be bothered with any more? What about mobile devices? Do they all have unique, strong passwords? Of course they don’t!
Do you even remember the passwords for once used services like MySpace, ICQ, your old email provider, etc? Did you delete any of these old accounts when you stopped using the service?
So chances are, at least some services share passwords. At least some are likely sharing a weak password (say eight characters or less).
Alright, so at the very least you’ve compartmentalised your risk, and made sure you’re using unique, strong passwords for Paypal, email, the bank, eBay etc, and compromising a little for passwords to sports and gaming sites, and the few forums you use? No? Oh, this isn’t looking so good…
Password Security “Recommendations”
So, before I go any further, let’s take a quick look at some of the oft quoted recommendations for good, secure passwords:
Well I don’t know about you, but I have no chance at all of meeting that little list based on passwords I’m expected to actually remember. Dozens of complex passwords across numerous services and devices, and I’m expected to change them quarterly. For 30, 50 or more services? Don’t be ridiculous…
OK, what we have here is a system for confusion and folks keeping all their passwords in a text file on their laptop, or a post-it on the lid that they can refer back to every time.
Which means if the laptop is ever stolen the thief gets quick and easy access to Facebook, Twitter, LinkedIn, Google, email, a bank account or three, paypal, eBay and who knows what else…
Given that many services insist on you using email address, which typically does not change, getting the starting point for attacking your account is reasonably easy.
OK, so what about user names, they’ll be better, right? Not really. Are you re-using usernames all over the place? Of course you are, as no one told you otherwise was a bad idea. Chances are many of your usernames are based around your name and initials. So I don’t really need to know that much about you to get a starting point that I pretty much know is you, and can throw a few million password attempts at.
Hang on a minute, surely most websites are going to lock me out after just a few failed attempts? Surprisingly many won’t. A depressing amount will let you keep trying over and over indefinitely…
No, that’s never going to work.
I think it’s time to stop relying on “the user” to pick a reasonable, unique strong password, don’t you?
Website Security
Far too often a news, blog, or small service or store is getting their website hacked
and their entire user database stolen. It’s not rare for them to get credit card, address
and other info. It’s frequently posted publicly on the web so anyone at all can go take a look. Often it’s been someone pretty big and well known – Sony, Gawker, LinkedIn…
It seems like it’s near enough every day that some news site is reporting the latest breach, or dumping of another database to pastebin.com
Why?
Simple – most websites are not banks or security companies. The developers don’t believe it’s going to need complex layers of protection and security as it’s just not important enough. The site is developed with “enough” security (often a simple password, username and simplistic hashing of the password for storage).
Not being a “secure” service, they decide there’s no need (supposedly) for limiting login attempts, there’s no need to put in delays between attempts. Not being a bank there’s “no need” for complex or computer intensive methods of securing that data. Trouble is, because so many of those user types share passwords across multiple services, the fastest way to get a hold of some paypal or banking passwords is to hack one of these “unimportant” websites.
If I can get into some website I get hundreds, or tens of thousands of emails+passwords, possibly with address, phone and credit card info too. Once I’ve got that database, I can run some software to test billions of possible passwords a second (and other, far more sophisticated techniques), until I have some, or most – depending on whether I want to wait an hour or a few days or weeks…
Let’s say I can steal let’s say FancyElectronics.com’s user database, I can be pretty sure that a frightening percentage of their users are using the same password on Facebook, banking, and/or their email. Let’s be generous and say around 5%. That’s an awful lot of accounts I can go digging in and simply try the passwords I’ve gained against many of the popular services.
So I take every user I’ve managed to get a password for from this big database, and now I try the same password on Paypal, Facebook, gmail, etc. It is pretty much guaranteed there will be a lot of matches.
This is so much easier than trying to steal just one person’s account, and gives so much
more!
Once I’ve got into a Facebook account or two, or email, chances are I can very rapidly get enough additional information about you to go and have a go at your online banking.
Lottery win. Thanks! I’ll be in the Bahamas working through the rest of the list.
Hmm, passwords are starting to seem pretty broken overall, aren’t they? Given how much attacking techniques have improved in recent years, especially with the leak of some very high profile databases containing millions of REAL passwords, I’d say passwords are starting to look very broken.
So what’s some alternatives?
Password Managers
Even though this is rather putting all your eggs in one basket, they work as the password database is local, secured by a really strong password (Nope, Fido32! is still not going to work), but allows you to give every website a truly unique password, and of a good length and randomness to ensure strength, such as “kp6yhX=vB,q=h_jrDeoN(y!-pij;s.”. Clearly you’re never going to remember any of these, but that’s rather the point.
They succeed as they give each website a truly lengthy (difficult to break), unique (not going to be found in someone’s leaked database), and pattern free.
For Smartphones, Windows and Mac, try taking a look at 1Password. Sadly there’s no Linux release – hopefully soon.
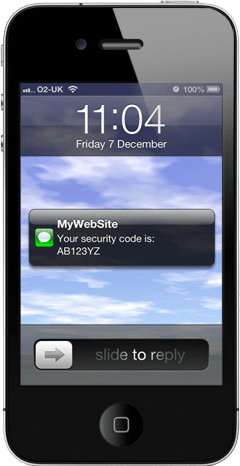 Two Factor Authentication
Two Factor Authentication
Probably the best increase in security in common use. Why? Because it takes the security
in part away from the users. No longer do you have to rely on your users picking sensible passwords, or not sharing it with everyone, or not putting it on a post-it note, or not using the same secure password everywhere (Fido32).
As we discussed last week, two factor authentication relies on two routes to the user. By using a secure token, or uniquely generated code sent via SMS we can have a lot more certainty that we’re actually communicating with the user, rather than a hacker.
Where multi-factor authentication can fall down is in looking at what the web service or app does when the user says they are without access to the device right now. If the site drops back to simple password authentication, well the second factor has just been rendered pointless. If you’re providing some simple fallback via email + security question, you’ve just blown your two factor authentication out of the water. Better would be to provide access, but with some requirement to validate via the second factor or phone call within a certain time-frame or be locked out and transactions nullified. Perhaps within a day or two.
It’s not perfect – nothing is, but there’s little point using it if a hacker can simply turn off the additional security by claiming the device is not to hand. In that case there is no additional security.
This is where implementing via SMS can be a win – it is near universal, rather than relying on a token or token-generating app that is probably not going to support every platform. Don’t forget those who don’t yet have a smartphone or have spotty internet access.
Just don’t provide an easy route to turn off the second factor, or it’s entirely pointless.
 Biometrics
Biometrics
Like the fingerprint scanner in your laptop? Or the fancy stuff beloved of Hollywood?
Laughter
These “appear” to be secure, and will frequently have you thinking that you have additional security.
The first problem from a security point of view is that biometrics are (allegedly) unique, but they are not secret.
So they can identify you superbly, but they cannot reasonably be used for security.
For as long as they have existed that have been a succession of news pieces pointing out that flaws often mean these devices can significantly lower your security!
In one notable case a brand of fingerprint scanner (UPEK) used by dozens of manufacturers basically stored Windows passwords in the registry, in the clear. So essentially removing all security from the machines in question.
Not convinced? There’s a nice article on the dangers of conflating identity and authorisation from Microsoft Technet. Yes the same Microsoft who used to sell a little toy fingerprint scanner that would log you into Windows. Oh well.
Conclusion
Currently it seems passwords are running out of time, and there’s precious few brilliant ideas on the horizon. Some of the no password ideas of security seem interesting, but I’m not sure any are ready for production use yet. For now the best approach appears to be multi-factor authentication, so long as you’re remembering not to provide an easy opt-out or way of bypassing once someone has opted in to multi factor authentication.



